Do you have legacy applications that worry you? Are you still waiting for a security patch? Some months ago, Microsoft released the Enhanched Mitigation Experience Toolkit v2.1 (EMET), a powerful configuration utility that will help you harden Windows applications.
For more details here: The one security tool every Windows user should know about | ZDNet
From Microsoft’s Download Center:
Overview
The enhanced Mitigation Experience Toolkit (EMET) is designed to help prevent hackers from gaining access to your system.
Software vulnerabilities and exploits have become an everyday part of life. Virtually every product has to deal with them and consequently, users are faced with a stream of security updates. For users who get attacked before the latest updates have been applied or who get attacked before an update is even available, the results can be devastating: malware, loss of PII, etc.
Security mitigation technologies are designed to make it more difficult for an attacker to exploit vulnerabilities in a given piece of software. EMET allows users to manage these technologies on their system and provides several unique benefits:
1. No source code needed: Until now, several of the available mitigations (such as Data Execution Prevention) have required for an application to be manually opted in and recompiled. EMET changes this by allowing a user to opt in applications without recompilation. This is especially handy for deploying mitigations on software that was written before the mitigations were available and when source code is not available.
2. Highly configurable: EMET provides a higher degree of granularity by allowing mitigations to be individually applied on a per process basis. There is no need to enable an entire product or suite of applications. This is helpful in situations where a process is not compatible with a particular mitigation technology. When that happens, a user can simply turn that mitigation off for that process.
3. Helps harden legacy applications: It’s not uncommon to have a hard dependency on old legacy software that cannot easily be rewritten and needs to be phased out slowly. Unfortunately, this can easily pose a security risk as legacy software is notorious for having security vulnerabilities. While the real solution to this is migrating away from the legacy software, EMET can help manage the risk while this is occurring by making it harder to hackers to exploit vulnerabilities in the legacy software.
4. Ease of use: The policy for system wide mitigations can be seen and configured with EMET’s graphical user interface. There is no need to locate up and decipher registry keys or run platform dependent utilities. With EMET you can adjust setting with a single consistent interface regardless of the underlying platform.
5. Ongoing improvement: EMET is a living tool designed to be updated as new mitigation technologies become available. This provides a chance for users to try out and benefit from cutting edge mitigations. The release cycle for EMET is also not tied to any product. EMET updates can be made dynamically as soon as new mitigations are ready
The toolkit includes several pseudo mitigation technologies aimed at disrupting current exploit techniques. These pseudo mitigations are not robust enough to stop future exploit techniques, but can help prevent users from being compromised by many of the exploits currently in use. The mitigations are also designed so that they can be easily updated as attackers start using new exploit techniques.
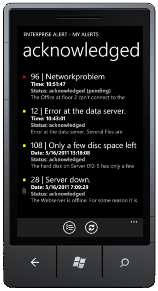 Every IT administrator is sleeping with one eye open to check for the status of the infrastructure under his responsibility. To help into this direction, Derdack, based in Potsdam, released a new enterprise alerting app for Windows Phone 7, message master® Enterprise Alert. The app enables Microsoft System Center Operations Manager (SCOM), Service Manager (SCSM), HP Operations Center and IBM Tivoli Monitoring users to manage business critical incidents directly from a WP7 smartphone.
Every IT administrator is sleeping with one eye open to check for the status of the infrastructure under his responsibility. To help into this direction, Derdack, based in Potsdam, released a new enterprise alerting app for Windows Phone 7, message master® Enterprise Alert. The app enables Microsoft System Center Operations Manager (SCOM), Service Manager (SCSM), HP Operations Center and IBM Tivoli Monitoring users to manage business critical incidents directly from a WP7 smartphone.